Understand the baffling technology words and phrases you hear every day.
The Internet
What is a Browser
What is Cache
What is a Cookie
What is Data in Transit
What is Data at Rest
What is a Data Packet
What is DNS
What is Encryption
What is End-to-End Encryption
What is HTTP/HTTPS
What is SSL/TLS
Your Company Network
What is Antivirus Software
What is DNS Content Filtering
What is Advanced Endpoint Security
What is a Firewall
What is a Modem
What is a Network
What is Remote Desktop (RDP)
Work from Anywhere
What is a Home Network
What is a Hotspot
What is a VPN
What is Wi-Fi
Life in the Cloud
What is the Cloud
Your Company Assets
What is Access Rights
What is a Data Inventory
What is Shadow IT
What is a Software Inventory
What is a Technology Roadmap
What is IT Asset Management (ITAM)
What are User Access Rights
Your Security Essentials
What is a Brute Force Attack
What is Credential Stuffing
What is an IP Blacklist
What is a Keylogger
What is Malware
What is Warshipping
What is a Whitelist
What is a Browser
What is Cache
What is a Cookie
What is Data in Transit
What is Data at Rest
What is a Data Packet
What is DNS
What is Encryption
What is End-to-End Encryption
What is HTTP/HTTPS
What is SSL/TLS
Your Company Network
What is Antivirus Software
What is DNS Content Filtering
What is Advanced Endpoint Security
What is a Firewall
What is a Modem
What is a Network
What is Remote Desktop (RDP)
Work from Anywhere
What is a Home Network
What is a Hotspot
What is a VPN
What is Wi-Fi
Life in the Cloud
What is the Cloud
Your Company Assets
What is Access Rights
What is a Data Inventory
What is Shadow IT
What is a Software Inventory
What is a Technology Roadmap
What is IT Asset Management (ITAM)
What are User Access Rights
Your Security Essentials
What is a Brute Force Attack
What is Credential Stuffing
What is an IP Blacklist
What is a Keylogger
What is Malware
What is Warshipping
What is a Whitelist
What is Data in Transit?
Data in transit, also called data in motion, is data that is actively moving from one location to another. This can be across the internet, within a private network, or from one device to another.
So much of what we do daily involves data in transit. Sending an email, browsing online, accessing cloud applications, and sending a text all create data in transit.
How is This Data Protected?
As your data moves across the internet or a private network, it passes through several servers, exchanging information (handshakes) before it reaches its destination. It isn't a single point A to point B "hello" "I got it" communication. This means opportunities for the wrong people to access your data.
End-to-end encryption is recommended for secure data exchange. This ensures that data is encrypted so that only the sender and receiver can access it.
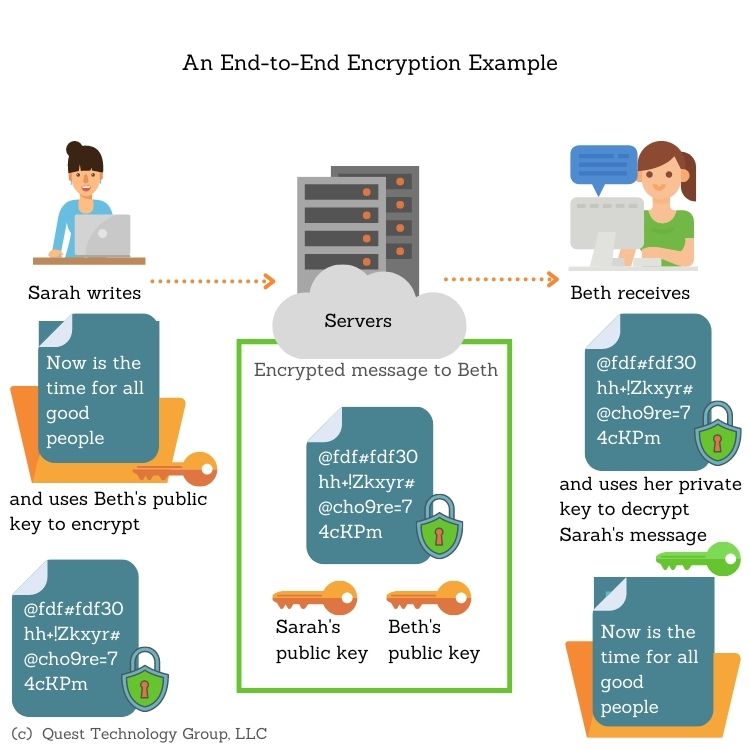
What is Data at Rest?
As its name implies, data at rest is data that is not actively moving. It is data stored on a hard drive or archived to a storage device. For example, email stored in your email application such as Outlook, and files stored on your laptop are both data at rest.
How is This Data Protected?
While it can seem that idle data is safe from unauthorized access, this is not the case. Anyone with access to your device or network storage can easily grab the data. Consider this --- when you save a file to your laptop, it is saved in the same plaintext format as created. When anyone opens the file, it is readable. This is why data at rest should be encrypted.
The best practice is to encrypt the data as well as all storage devices.
Companies should start by identifying all their sensitive data. Where does this data live? How is it accessed? Who has access to it? The data inventory will vary with each company and will continually change.
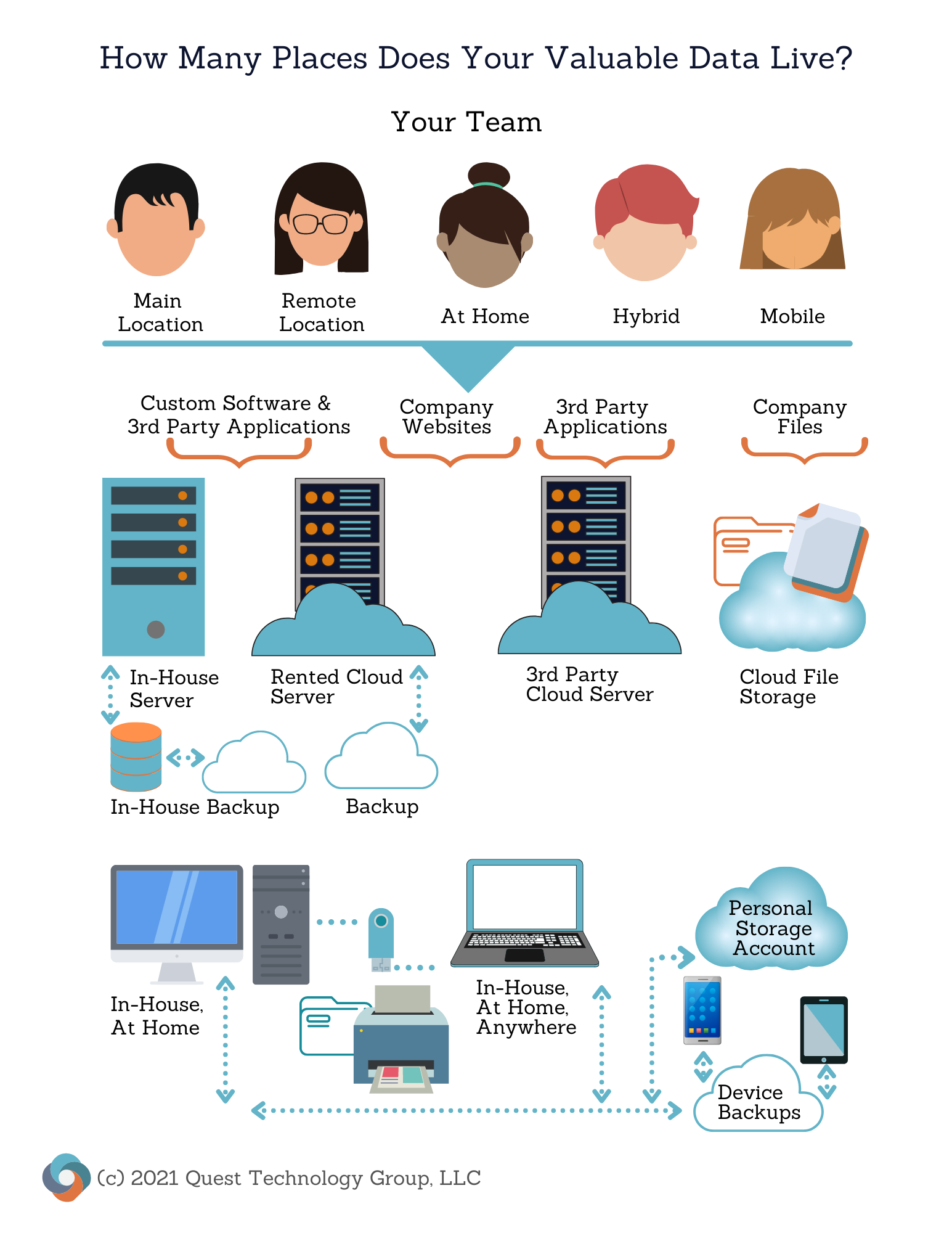
Data management should be an ongoing company commitment to protect both the company's and its clients' and customers' valuable data.
Keep Learning
What is Encryption?
What is End-to-End Encryption?
