Why Every Company Needs Cybersecurity Protection That Aligns With Their Business Goals
There was a time not so long ago when only big companies were concerned with cybersecurity. Not so any more. Size doesn’t matter. Every company has valuable information that today's bad actors are eager to steal.
How many of these cybersecurity misperceptions sound familiar?
We have backups. We'll just recover our lost files.
We're a small company. No one will bother us.
We have antivrus software so we're protected.
We don't have anything worth stealing.
We're in the cloud so we're protected.
Our MSP takes care of this for us.
We have cyber insurance.
It's complicated.
It's expensive.
We're a small company. No one will bother us.
We have antivrus software so we're protected.
We don't have anything worth stealing.
We're in the cloud so we're protected.
Our MSP takes care of this for us.
We have cyber insurance.
It's complicated.
It's expensive.
If you said "Yes!" to even one of these, you're not alone. But there's more to consider than just protecting your company. You have valued customers and clients who trust you to protect them too. Fortunately, implementing the right cybersecurity protection for your company doesn't have to be complicated or expensive.
The first step is to commit to a security awareness mindset throughout your company. It starts with committed leadership and step-by-step actions.
The first step is to commit to a security awareness mindset throughout your company. It starts with committed leadership and step-by-step actions.
Who's Responsible for Implementing and Monitoring Your Company's Cybersecurity Protection?
Fact: Cybersecurity is a company-wide responsibility. It starts at the top with committed leaders who continually listen, learn, share their knowledge, and create a culture of shared security compliance.
Cybersecurity isn't a series of one-and-done checkboxes that can or should be handed off to IT to do. A commitment to the responsible safeguards for company assets, employees, customers, and all trusted business partners starts with the C-suite. The right IT team will contribute to the planning, execution, and continuous monitoring of all systems and resources.
The skills to implement a robust cybersecurity plan have changed. Your valued IT team who keeps the day-to-day plates spinning might not have the cybersecurity skills necessary. That's okay. You just need to have the right information to understand who does what, the skills required, and then the steps to build the right team with each member contributing.
This technology team roles matrix is also included in the 18 Questions to Ask Your IT Team About Your Cybersecurity Protection in 2026.
Tips for Creating Your Step-by-Step Cybersecurity Program
Every company has its own goals, plans, needs, and resources so there is no easy, one-size-fits-all cybersecurity solution. But there are proven action steps that every company can adopt to guide their security decision-making.
Clarify your cybersecurity risk tolerance
How much can you afford to lose when a security event happens?
High risk tolerance: You're able to withstand larger financial and reputational losses. Your focus is on maximizing profits at the expense of short-term losses.
Moderate risk tolerance: You seek a balance between risk impacts and potential profits from taking risks.
Low risk tolerance: Your priority is minimizing loss, negative events, and damage to your company.
Clarify your cybersecurity risk appetite
How much risk are you willing to assume to achieve your long-term goals and strategies?
High risk appetite: This goes hand in hand with high risk tolerance. You are a risk-taker in anticipation of high rewards.
Moderate risk appetite: You're likely to take risks within your comfort zone.
Low risk appetite: You fall into the risk averse category. You are willing to sacrifice higher returns in both the short and long term for less risk exposure.
Discover your cybersecurity risk comfort zone
Every leader and company has its own cybersecurity comfort zone, the place where risk tolerance and risk appetite meet.
Start your cybersecurity planning there.
We're business owners and leaders like you are so we understand that sifting through the noise and information is sometimes just too much.
Here's a short ebook, Discovering Your Company's Unique Risk Posture, that you can read at your leisure. It includes a plain English explanation of the two risk types, how they impact your company's goals, and how to use these assessments to gain clarity and focus.
Grab Your Free Copy
Here's a short ebook, Discovering Your Company's Unique Risk Posture, that you can read at your leisure. It includes a plain English explanation of the two risk types, how they impact your company's goals, and how to use these assessments to gain clarity and focus.
Grab Your Free Copy
Conduct an IT asset discovery
Explore the Details
Then build your documented, actionable roadmap
The results of your technology asset discovery are the foundation for your technology planning. Every company is different, and how you address the results of your discovery should be appropriate for your company.
Consider your cybersecurity risk comfort zone. Include cybersecurity compliance requirements from third parties such as insurance coverages, regulatory compliance, business partners, and customers' compliance requirements.
Detail small, actionable steps.
Plan. Execute. Measure. Modify. Repeat.
The 3 Essential Cybersecurity Protections Every Company Can Implement Now
1. Replace Legacy Antivirus With Proactive Endpoint Protection
Legacy antivirus software is primarily reactive.
That means it waits to be told what potential malware it should look for. The time delay between the discovery of a new virus and the download of the software update to your company's devices leaves you at significant risk.
Antivirus updates are generally released on a fixed schedule instead of as soon as they are available. The need for quick response is critical.
Each team member often has access to the antivirus settings on his desktop or laptop. There is no centralized management to ensure all devices are updated as quickly as possible.
That means it waits to be told what potential malware it should look for. The time delay between the discovery of a new virus and the download of the software update to your company's devices leaves you at significant risk.
Antivirus updates are generally released on a fixed schedule instead of as soon as they are available. The need for quick response is critical.
Each team member often has access to the antivirus settings on his desktop or laptop. There is no centralized management to ensure all devices are updated as quickly as possible.
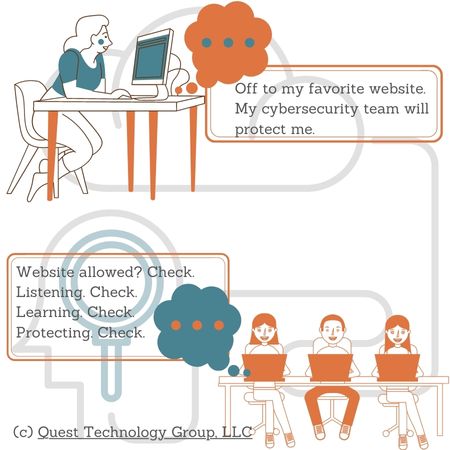
2. Add Next Generation Advanced Endpoint Security
Next generation security protection is proactive. That's a big deal.
It's like your company's moat. Next generation antivirus is continously listening, learning, and denying entry to anyone who it thinks is an attacker.
The response is immediate. No waiting to be told what to do next.
Since this is proactive centralized protection, everyone in your company has the same continous level of security. No downloads, no overlooked devices.
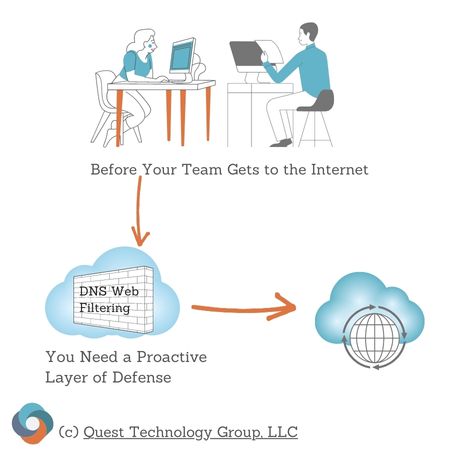
3. Implement DNS Web Content Filtering
Working online is a way of life for every company. Website access, even ones we believe can be trusted, introduce an additional level of risk that you can reduce.
DNS content filtering, also referred to as web filtering, prevents exposure to malware, malicious, and suspected websites before your team members can access them.
Adding this level of protection is applied to everyone regardless of where they're working. In today's hybrid, remote, mobile, office, home work environment, a consistent security framework is just wise business.
DNS content filtering, also referred to as web filtering, prevents exposure to malware, malicious, and suspected websites before your team members can access them.
Adding this level of protection is applied to everyone regardless of where they're working. In today's hybrid, remote, mobile, office, home work environment, a consistent security framework is just wise business.
What About Cyber Insurance?
Myth: We've heard business leaders say they have cyber insurance coverage so they're not concerned about security risks. Their insurance company has them covered. Not so.
What is Cyber Insurance?
Cyber liability is specialized business insurance coverage. This coverage is in addition to your company's general liability insurance policy and is often specifically excluded under this policy. Every insurance company has its own set of coverages, limitations, and exclusions so a careful review with your insurance agent, broker, or company representative is essential.
What is Covered by Cyber Insurance?
According to the FTC's cybersecurity resources for small business, these are coverages you should have included in your cyber insurance policy:
What Are Insurance Companies Requirements for Cyber Liability Coverage?
Regardless of your current insurance carrier or policy, it is important to keep these points in mind: